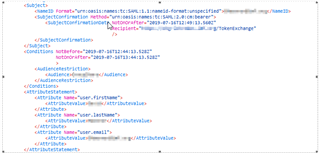
We need to hide Groupshare application server behind transparent proxy – WebSeal. WebSeal provides another authentication that is very important for us before it sends request to backend server. Unfortunately it seems that Groupshare application server needs some http header, but this is lost when going through WebSeal and user authentication fails on /api/management/v2/users. I have not found anything helpful in Knowledge Base. I would like to ask whether it is possible to use some configuration that would provide running application server behind WebSeal. If you have some experience, if it is possible and how much would the support of supplier cost in this case.
About WebSeal: https://www.ibm.com/support/knowledgecenter/SSPREK_9.0.5/com.ibm.isam.doc/wrp_config/concept/con_ws_authe.html

 Translate
Translate